7, Dec 2023
The Network Mapper: Exploring Security In The Land Of Enchantment
The Network Mapper: Exploring Security in the Land of Enchantment
Related Articles: The Network Mapper: Exploring Security in the Land of Enchantment
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to The Network Mapper: Exploring Security in the Land of Enchantment. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
The Network Mapper: Exploring Security in the Land of Enchantment

The Network Mapper, more commonly known as Nmap, is a powerful and versatile open-source tool used for network discovery and security auditing. It has become an indispensable resource for cybersecurity professionals, network administrators, and researchers worldwide. This article delves into the significance of Nmap in the context of New Mexico, highlighting its role in safeguarding critical infrastructure, enhancing cybersecurity awareness, and fostering a thriving cybersecurity ecosystem within the state.
Nmap’s Importance in New Mexico’s Cybersecurity Landscape
New Mexico, like many states, faces a unique set of cybersecurity challenges. Its sprawling landscape, vast energy infrastructure, and growing technological dependence make it a target for cyberattacks. Nmap emerges as a crucial tool for addressing these challenges, providing a comprehensive approach to network security analysis and vulnerability assessment.
1. Protecting Critical Infrastructure:
New Mexico’s critical infrastructure, including energy production, water systems, and telecommunications, is vital to its economic well-being and national security. Nmap plays a critical role in securing these assets by:
- Network discovery and mapping: Nmap enables network administrators to identify all devices connected to their network, including those that may be unauthorized or unknown. This provides a clear picture of the network landscape, allowing for better security posture.
- Vulnerability scanning: Nmap can identify known security vulnerabilities in network devices, operating systems, and applications. This information allows for proactive remediation, reducing the risk of exploitation.
- Port scanning: Nmap can scan for open ports on network devices, revealing potential entry points for attackers. This information helps in hardening security measures and closing potential vulnerabilities.
2. Enhancing Cybersecurity Awareness:
Nmap plays a vital role in fostering cybersecurity awareness among individuals, organizations, and communities in New Mexico. It empowers users to understand the importance of network security and to take proactive steps to protect their systems.
- Educational tool: Nmap’s open-source nature allows for widespread accessibility, making it an ideal educational tool for students, professionals, and hobbyists. Learning to use Nmap fosters a deeper understanding of network security principles and best practices.
- Community engagement: Nmap’s online community provides a platform for users to share knowledge, discuss best practices, and collaborate on security research. This fosters a sense of collective responsibility for cybersecurity and promotes knowledge sharing across the state.
3. Fostering a Thriving Cybersecurity Ecosystem:
Nmap’s widespread adoption and its role in cybersecurity education and research contribute to a thriving cybersecurity ecosystem in New Mexico. This ecosystem attracts skilled professionals, fosters innovation, and helps to address the growing need for cybersecurity expertise.
- Talent development: Nmap’s accessibility and educational value encourage the development of skilled cybersecurity professionals in New Mexico. This talent pool is crucial for securing the state’s critical infrastructure and protecting its citizens.
- Research and innovation: Nmap’s open-source nature fosters a culture of collaboration and innovation in the cybersecurity field. Researchers and developers in New Mexico can leverage Nmap to develop new tools and techniques for network security analysis and vulnerability assessment.
Nmap’s Impact on New Mexico’s Cybersecurity Landscape
The impact of Nmap on New Mexico’s cybersecurity landscape is significant. Its adoption by businesses, government agencies, and individuals has led to a greater awareness of network security threats and vulnerabilities. This has resulted in:
- Improved security practices: Organizations in New Mexico are increasingly implementing best practices for network security, including regular vulnerability scanning, port hardening, and intrusion detection systems. This has significantly reduced the risk of successful cyberattacks.
- Enhanced incident response: Nmap’s ability to quickly identify compromised systems and vulnerabilities has improved incident response capabilities in New Mexico. This allows for faster containment of breaches and minimizes the impact of cyberattacks.
- Increased cybersecurity investment: The growing awareness of cybersecurity threats has led to increased investment in cybersecurity solutions, including security software, hardware, and personnel. This investment strengthens the state’s overall cybersecurity posture.
Nmap: A Powerful Tool for Security Professionals
Nmap’s versatility and power make it a valuable tool for security professionals in New Mexico. Its various features and capabilities allow for a comprehensive approach to network security analysis and vulnerability assessment.
Key Features of Nmap:
- Network discovery: Nmap can identify all devices connected to a network, including those that may be hidden or disguised. This allows for a complete understanding of the network topology.
- Port scanning: Nmap can scan for open ports on network devices, revealing potential entry points for attackers. This information helps in hardening security measures and closing potential vulnerabilities.
- Operating system detection: Nmap can identify the operating system running on a device, providing valuable information for vulnerability assessment and exploit development.
- Vulnerability scanning: Nmap can identify known security vulnerabilities in network devices, operating systems, and applications. This allows for proactive remediation, reducing the risk of exploitation.
- Service detection: Nmap can identify the services running on a device, providing insights into potential attack vectors and security risks.
- Network mapping: Nmap can create a visual representation of a network, showing the connections between devices and their relationships to each other. This provides a clear picture of the network landscape.
Nmap’s Use Cases in New Mexico:
- Security audits: Nmap is used by security professionals to conduct regular audits of networks and systems to identify vulnerabilities and potential security risks.
- Penetration testing: Nmap is a key tool for penetration testers, who use it to simulate attacks and identify security weaknesses in systems.
- Incident response: Nmap is used by incident responders to quickly identify compromised systems and vulnerabilities, allowing for faster containment of breaches.
- Network monitoring: Nmap can be used to monitor network activity, identify anomalies, and detect potential threats.
- Research and development: Nmap is used by cybersecurity researchers to develop new tools and techniques for network security analysis and vulnerability assessment.
FAQs about Nmap in New Mexico:
1. Is Nmap legal to use in New Mexico?
Yes, Nmap is legal to use in New Mexico as long as it is used for legitimate purposes, such as security auditing, penetration testing, and research. However, it is important to be aware of the laws and regulations governing network scanning and to obtain permission before scanning any network that you do not own or control.
2. Is Nmap only for cybersecurity professionals?
While Nmap is a powerful tool for cybersecurity professionals, it can also be used by individuals and organizations with basic network security knowledge. There are many resources available online to help users learn how to use Nmap effectively.
3. How can I learn more about Nmap?
There are numerous resources available online to help you learn more about Nmap, including:
- Nmap’s official website: https://nmap.org
- Nmap’s documentation: https://nmap.org/book
- Online tutorials and courses: https://www.youtube.com/results?search_query=nmap+tutorial
4. What are some tips for using Nmap safely and effectively?
- Obtain permission: Before scanning any network that you do not own or control, obtain permission from the network owner or administrator.
- Use appropriate scan types: Nmap offers a variety of scan types, each with its own level of intrusiveness. Choose the scan type that is appropriate for your purpose.
- Avoid scanning critical infrastructure: Do not scan critical infrastructure, such as power grids, water systems, or telecommunications networks, without explicit permission.
- Respect privacy: Do not scan personal devices or networks without permission.
- Use Nmap responsibly: Nmap is a powerful tool that should be used responsibly. Avoid using it for malicious purposes or to cause harm to others.
Conclusion
Nmap plays a crucial role in safeguarding New Mexico’s critical infrastructure, fostering cybersecurity awareness, and driving a thriving cybersecurity ecosystem within the state. Its versatility, power, and accessibility make it an indispensable tool for individuals, organizations, and communities committed to enhancing network security and protecting against cyber threats. By embracing Nmap and its potential, New Mexico can continue to build a robust and resilient cybersecurity landscape, ensuring the security and well-being of its citizens and critical infrastructure.


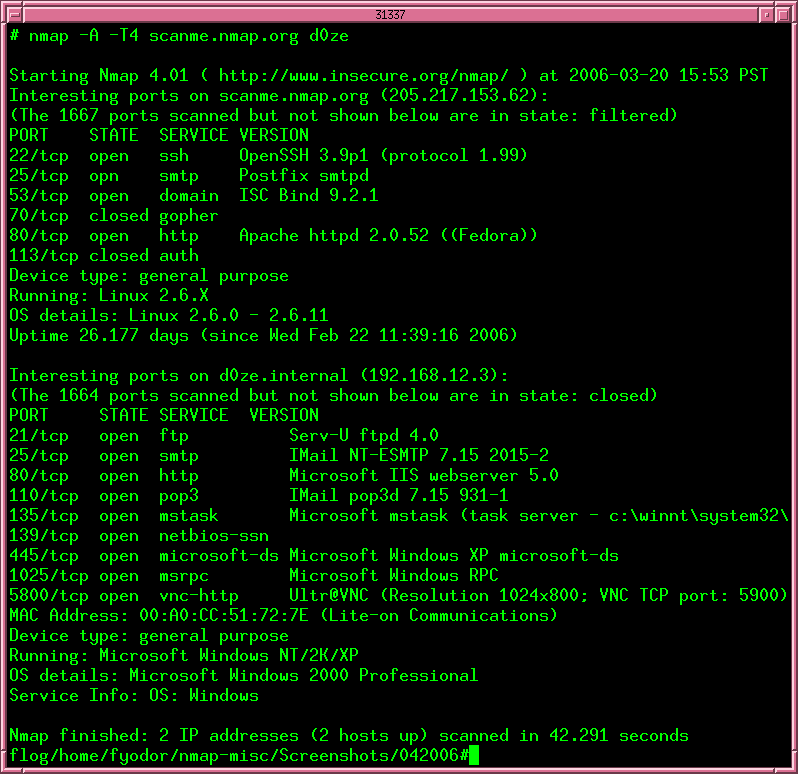



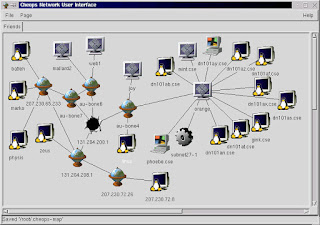
Closure
Thus, we hope this article has provided valuable insights into The Network Mapper: Exploring Security in the Land of Enchantment. We hope you find this article informative and beneficial. See you in our next article!
- 0
- By admin
