2, Sep 2023
The Significance Of Weak Hashing Algorithms In Network Security: A Comprehensive Analysis
The Significance of Weak Hashing Algorithms in Network Security: A Comprehensive Analysis
Related Articles: The Significance of Weak Hashing Algorithms in Network Security: A Comprehensive Analysis
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to The Significance of Weak Hashing Algorithms in Network Security: A Comprehensive Analysis. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: The Significance of Weak Hashing Algorithms in Network Security: A Comprehensive Analysis
- 2 Introduction
- 3 The Significance of Weak Hashing Algorithms in Network Security: A Comprehensive Analysis
- 3.1 Understanding Hashing Algorithms and Their Role in Security
- 3.2 The Perils of Weak Hashing Algorithms
- 3.3 Examples of Weak Hashing Algorithms
- 3.4 The Importance of Using Strong Hashing Algorithms
- 3.5 Mitigating the Risks of Weak Hashing Algorithms
- 3.6 FAQs Regarding Weak Hashing Algorithms
- 3.7 Tips for Avoiding Weak Hashing Algorithms
- 3.8 Conclusion
- 4 Closure
The Significance of Weak Hashing Algorithms in Network Security: A Comprehensive Analysis

The realm of network security relies heavily on robust cryptographic algorithms to safeguard sensitive data. However, the use of weak hashing algorithms can create vulnerabilities that compromise the integrity and confidentiality of information. This article delves into the significance of weak hashing algorithms, exploring their impact on network security, highlighting their shortcomings, and providing insights into how to mitigate the risks associated with their use.
Understanding Hashing Algorithms and Their Role in Security
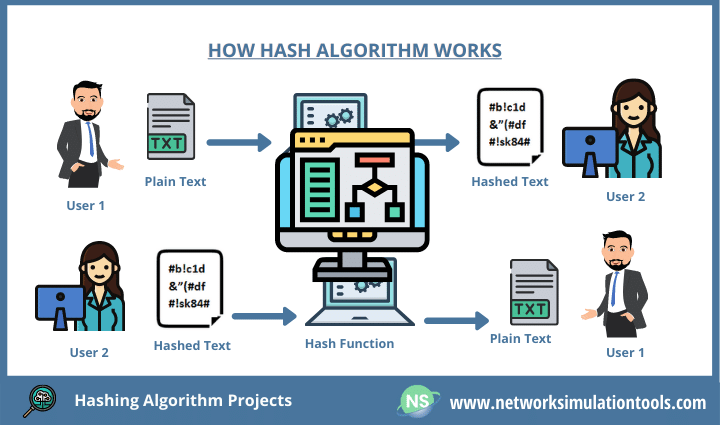
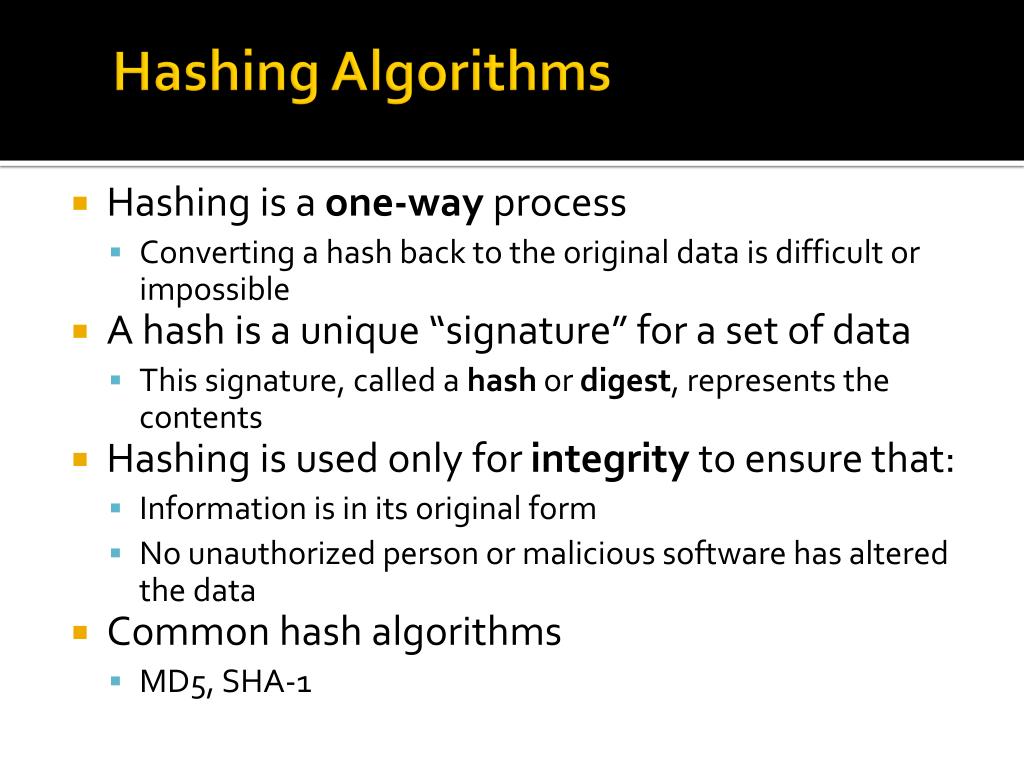
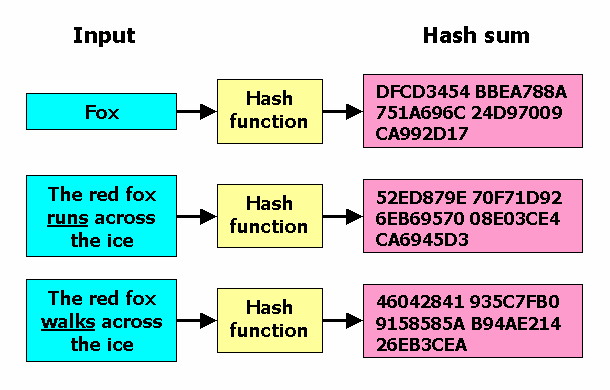
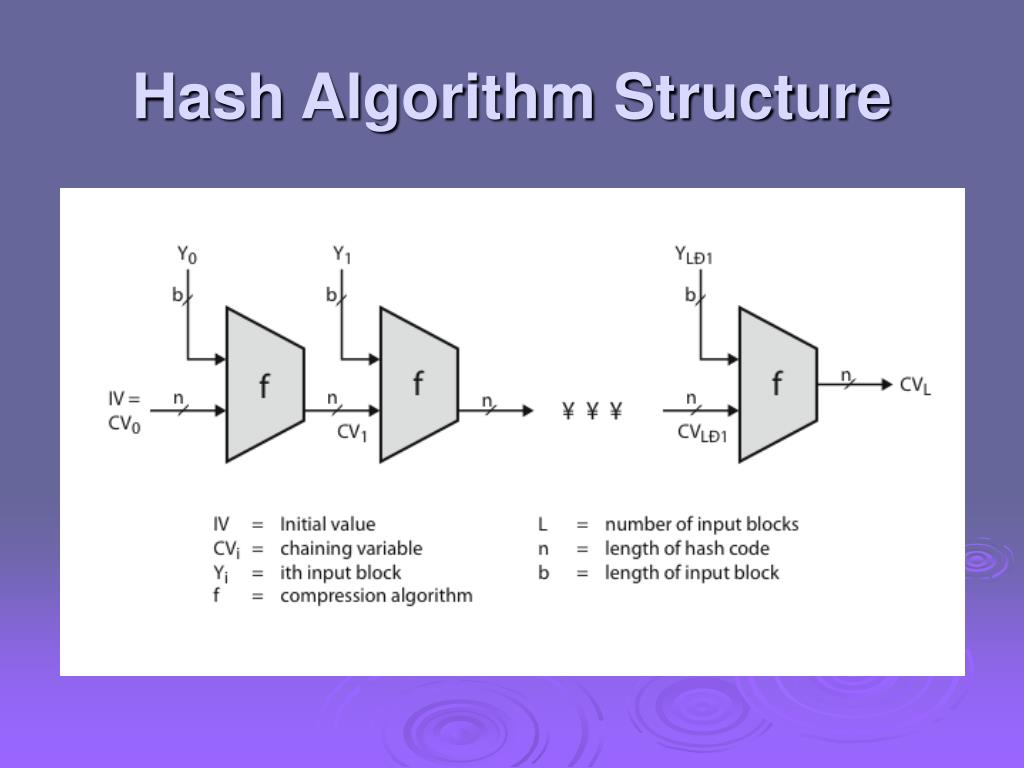
Hashing algorithms are mathematical functions that transform data of any size into a fixed-length string of characters, known as a hash or message digest. This process is irreversible, meaning that it is impossible to reconstruct the original data from its hash. Hashing algorithms play a crucial role in network security by providing mechanisms for:
- Data Integrity Verification: By comparing the hash of a file or message with its original hash, one can determine if any modifications have occurred during transmission. This ensures data integrity and prevents tampering.
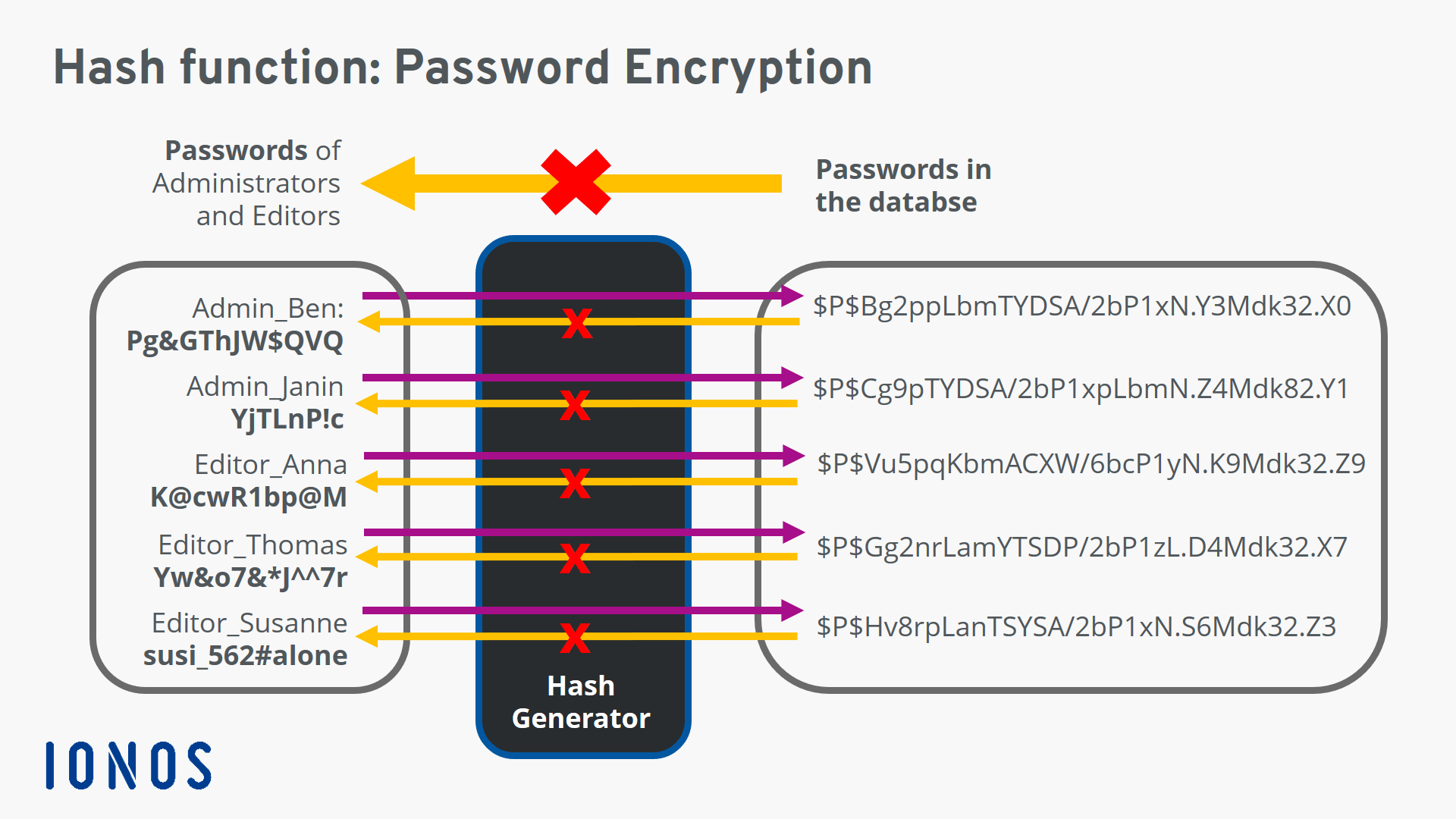
- Password Storage: Instead of storing passwords in plain text, which could be easily compromised, hashing algorithms convert passwords into secure hashes, making it difficult for attackers to retrieve the original password even if they gain access to the database.
- Digital Signatures: Hashing algorithms are used to create digital signatures, which are used to verify the authenticity and integrity of digital documents.
The Perils of Weak Hashing Algorithms
While hashing algorithms offer significant security benefits, the effectiveness of these algorithms hinges on their strength. Weak hashing algorithms are susceptible to various attacks, rendering them unsuitable for secure applications. Here’s a breakdown of the vulnerabilities associated with weak hashing algorithms:
- Collision Attacks: A collision occurs when two different inputs produce the same hash output. Weak hashing algorithms are more prone to collisions, allowing attackers to create malicious data with the same hash as legitimate data, enabling them to bypass security checks and potentially compromise systems.
- Rainbow Table Attacks: Rainbow tables are pre-computed tables that contain hash values for a vast number of possible inputs. Attackers can use these tables to quickly reverse-engineer a hash and determine the original password. Weak hashing algorithms are more susceptible to rainbow table attacks due to their limited output space.
- Brute-Force Attacks: Brute-force attacks involve systematically trying all possible combinations of characters to find the correct password. Weak hashing algorithms with shorter hash outputs are easier to crack using brute-force methods.
- Preimage Attacks: A preimage attack involves finding an input that produces a specific hash output. Weak hashing algorithms can be vulnerable to preimage attacks, allowing attackers to forge data with a specific hash value.
Examples of Weak Hashing Algorithms
Several hashing algorithms have been deemed weak due to their susceptibility to attacks. Some notable examples include:
- MD5 (Message Digest 5): MD5 was widely used in the past, but it has been found to be vulnerable to collision attacks. In 2004, researchers demonstrated the ability to create two different files with the same MD5 hash.
- SHA-1 (Secure Hash Algorithm 1): SHA-1 was designed as an improvement over MD5, but it also suffers from weaknesses and is considered insecure for cryptographic purposes.
- SHA-0: SHA-0 is a predecessor to SHA-1 and is considered even weaker, having been found to be susceptible to collisions.
The Importance of Using Strong Hashing Algorithms
To mitigate the risks associated with weak hashing algorithms, it is crucial to adopt strong and secure alternatives. Modern hashing algorithms, such as SHA-256 and SHA-512, offer significantly improved security compared to their predecessors. These algorithms have larger output spaces, making them more resistant to collisions and brute-force attacks.
Mitigating the Risks of Weak Hashing Algorithms
Here are some key strategies for mitigating the risks associated with weak hashing algorithms:
- Upgrade to Stronger Algorithms: Whenever possible, migrate to stronger hashing algorithms like SHA-256 or SHA-512. These algorithms offer greater resistance to attacks and provide a higher level of security.
- Implement Salt and Peppering: Salt and peppering involve adding random data to the input before hashing. This makes it more difficult for attackers to use pre-computed tables or brute-force methods to crack passwords.
- Use Secure Password Storage Practices: Employ secure password storage practices, such as storing passwords in a hashed format with a strong hashing algorithm and incorporating salt and peppering.
- Regularly Update Systems and Software: Keep systems and software up to date with the latest security patches and updates. This ensures that any vulnerabilities associated with weak hashing algorithms are addressed promptly.
FAQs Regarding Weak Hashing Algorithms
Q: What are the consequences of using a weak hashing algorithm?
A: Using a weak hashing algorithm can lead to various security breaches, including:
- Data Integrity Compromise: Tampered data can go undetected, leading to inaccurate information and potential financial losses.
- Password Theft: Attackers can easily crack weak hashes and gain access to sensitive accounts.
- Authentication Bypass: Malicious actors can exploit weaknesses in weak hashing algorithms to bypass authentication mechanisms.
Q: How can I determine if a system is using a weak hashing algorithm?
A: Several tools and techniques can help identify the use of weak hashing algorithms:
- Network Security Audits: Professional security audits can analyze systems and identify vulnerabilities related to weak hashing algorithms.
- Security Scanning Tools: Tools like Nmap can scan for vulnerabilities, including the use of weak hashing algorithms.
- Code Analysis: Analyzing the source code of applications can reveal the hashing algorithms used.
Q: What are some best practices for choosing a secure hashing algorithm?
A: When selecting a hashing algorithm, consider the following factors:
- Strength: Opt for algorithms with a proven track record of security and resistance to attacks.
- Speed: Choose an algorithm that provides a balance between security and performance.
- Availability: Ensure that the chosen algorithm is widely supported and implemented.
Tips for Avoiding Weak Hashing Algorithms
- Stay Updated: Keep abreast of the latest security recommendations and best practices regarding hashing algorithms.
- Consult Security Experts: Seek advice from security professionals to ensure you are using the most secure hashing algorithms for your specific needs.
- Use Trusted Sources: Download and install software from reputable sources to minimize the risk of encountering vulnerabilities related to weak hashing algorithms.
Conclusion
The use of weak hashing algorithms poses significant security risks, leaving sensitive data vulnerable to attacks. By understanding the vulnerabilities associated with these algorithms and adopting strong security practices, organizations and individuals can effectively mitigate these risks. Prioritizing the use of robust and secure hashing algorithms is crucial for safeguarding data integrity, password security, and overall network security. Regularly reviewing and updating security practices to incorporate stronger hashing algorithms and best practices is essential to ensure ongoing protection against evolving threats.



Closure
Thus, we hope this article has provided valuable insights into The Significance of Weak Hashing Algorithms in Network Security: A Comprehensive Analysis. We hope you find this article informative and beneficial. See you in our next article!
- 0
- By admin
