1, Nov 2023
Unmasking Vulnerability: A Comprehensive Guide To Nmap’s Cipher Detection Capabilities
Unmasking Vulnerability: A Comprehensive Guide to Nmap’s Cipher Detection Capabilities
Related Articles: Unmasking Vulnerability: A Comprehensive Guide to Nmap’s Cipher Detection Capabilities
Introduction
With great pleasure, we will explore the intriguing topic related to Unmasking Vulnerability: A Comprehensive Guide to Nmap’s Cipher Detection Capabilities. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
- 1 Related Articles: Unmasking Vulnerability: A Comprehensive Guide to Nmap’s Cipher Detection Capabilities
- 2 Introduction
- 3 Unmasking Vulnerability: A Comprehensive Guide to Nmap’s Cipher Detection Capabilities
- 3.1 Understanding the Significance of Cipher Detection
- 3.2 Nmap’s "ssl-enum-ciphers" Script: A Powerful Tool for Cipher Analysis
- 3.3 Unveiling the Benefits of Utilizing the "ssl-enum-ciphers" Script
- 3.4 FAQs: Addressing Common Queries Regarding "ssl-enum-ciphers"
- 3.5 Tips for Effective Cipher Detection and Remediation
- 3.6 Conclusion: Empowering Security Professionals with Nmap’s Cipher Detection Capabilities
- 4 Closure
Unmasking Vulnerability: A Comprehensive Guide to Nmap’s Cipher Detection Capabilities
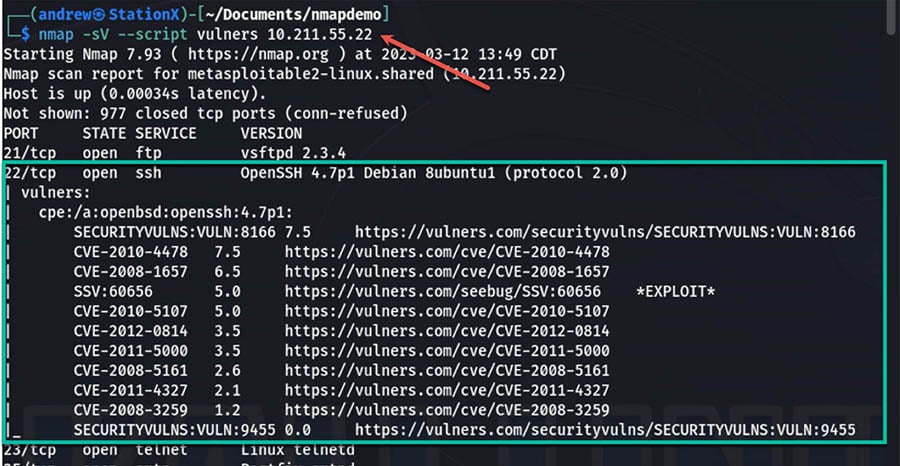
In the realm of network security, understanding the vulnerabilities present within a system is paramount. This knowledge empowers security professionals to proactively identify and mitigate potential risks before they can be exploited. One tool that plays a crucial role in this endeavor is Nmap, a powerful network scanner renowned for its versatility and depth of capabilities. Within its arsenal, Nmap boasts a dedicated script, aptly named "ssl-enum-ciphers," which serves as a beacon in the quest to identify weak cryptographic configurations within networked services.
Understanding the Significance of Cipher Detection
The digital landscape is increasingly reliant on secure communication channels. Sensitive data, such as financial transactions, personal information, and confidential business communications, traverses the internet, often relying on encryption protocols to safeguard its integrity. These protocols utilize a complex interplay of algorithms and keys to ensure secure data exchange. However, the effectiveness of these protocols hinges on the strength of the employed ciphers.
Weak ciphers, characterized by vulnerabilities that can be exploited to compromise encrypted data, pose a significant threat to security. Attackers can leverage these weaknesses to decrypt sensitive information, potentially leading to data breaches, identity theft, and financial loss. Recognizing and mitigating these vulnerabilities is crucial for maintaining a robust security posture.
Nmap’s "ssl-enum-ciphers" Script: A Powerful Tool for Cipher Analysis
Nmap’s "ssl-enum-ciphers" script emerges as a potent tool for detecting and analyzing the cryptographic configurations of network services. It meticulously probes target systems, identifying the supported ciphers, their respective strengths, and their vulnerabilities. This comprehensive analysis provides invaluable insights into the security posture of the targeted services.
The script’s capabilities extend beyond simple cipher identification. It delves deeper, uncovering critical information such as:
- Cipher Suite Support: It reveals the specific cipher suites supported by the target service, enabling the identification of outdated or insecure configurations.
- Key Exchange Algorithms: The script meticulously analyzes the key exchange algorithms employed by the service, pinpointing potential weaknesses in the key establishment process.
- Hashing Algorithms: It probes the hashing algorithms used by the service, highlighting any vulnerabilities associated with weak or compromised hashing functions.
- Protocol Versions: The script assesses the supported SSL/TLS protocol versions, identifying potential risks associated with outdated or insecure versions.
Unveiling the Benefits of Utilizing the "ssl-enum-ciphers" Script
The "ssl-enum-ciphers" script offers a multitude of benefits to security professionals, empowering them to:
- Proactively Identify Vulnerabilities: The script enables proactive identification of weak cipher configurations before they can be exploited by attackers, fostering a proactive security approach.
- Prioritize Remediation Efforts: By pinpointing specific weaknesses, the script facilitates the prioritization of remediation efforts, allowing security teams to focus on the most critical vulnerabilities first.
- Improve Security Posture: Identifying and addressing weak cipher configurations significantly enhances the overall security posture of networked services, reducing the risk of data breaches and other security incidents.
- Compliance Verification: The script aids in verifying compliance with industry standards and regulations, ensuring that systems adhere to best practices for secure communication.
- Enhance Threat Intelligence: The script’s output provides valuable insights into the security landscape, enriching threat intelligence and enabling informed decision-making.
FAQs: Addressing Common Queries Regarding "ssl-enum-ciphers"
Q: What are the prerequisites for using the "ssl-enum-ciphers" script?
A: To utilize the "ssl-enum-ciphers" script, ensure that Nmap is installed on your system. The script is typically bundled with Nmap, but it may require additional configuration or dependencies depending on the specific Nmap version and operating system.
Q: How do I incorporate the "ssl-enum-ciphers" script into my Nmap scans?
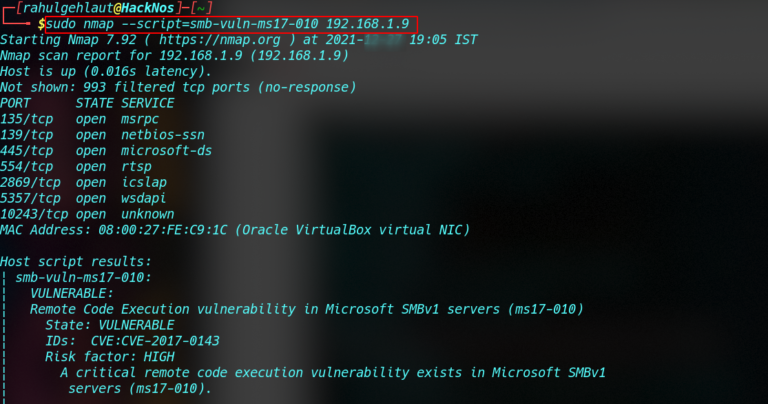
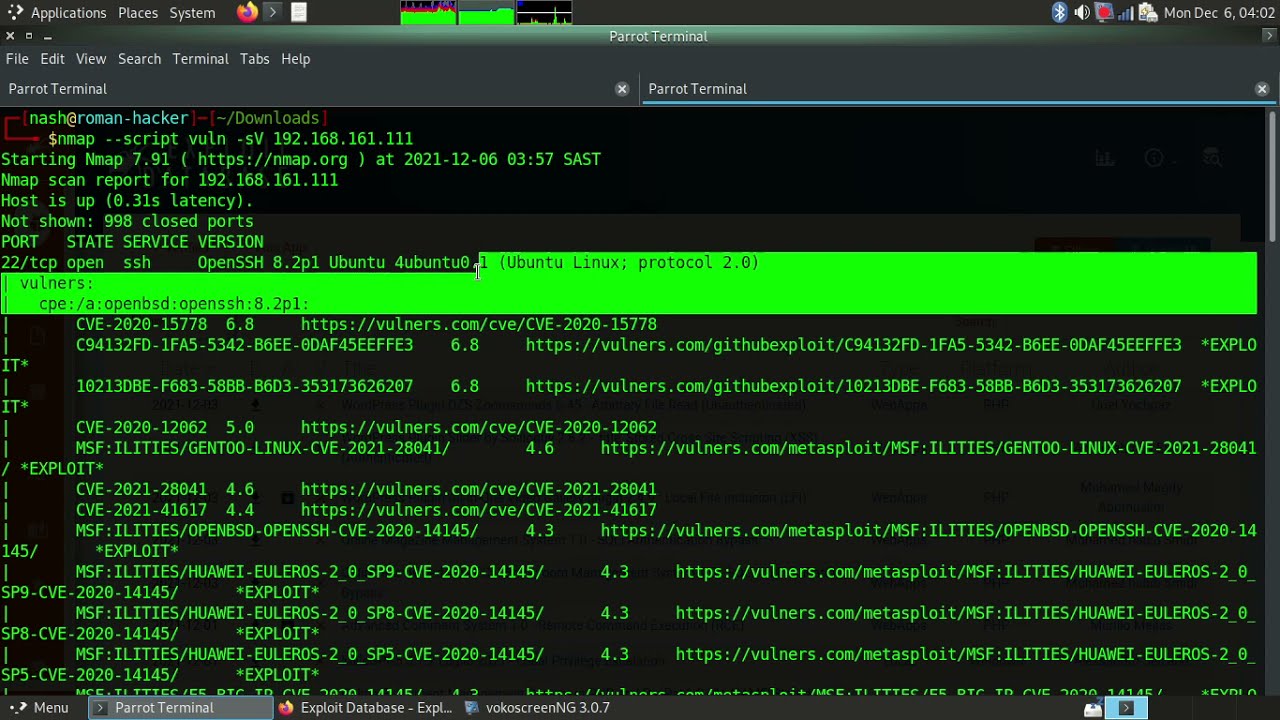
A: The "ssl-enum-ciphers" script is executed as part of an Nmap scan. It is invoked using the --script flag followed by the script name. For example, to scan the target host at IP address 192.168.1.100 and execute the "ssl-enum-ciphers" script, you would use the command:
nmap -sV -p 443 --script ssl-enum-ciphers 192.168.1.100Q: How do I interpret the output generated by the "ssl-enum-ciphers" script?
A: The script’s output provides detailed information about the supported ciphers, key exchange algorithms, hashing algorithms, and protocol versions. The output is typically organized into tables and lists, making it easy to analyze and interpret.
Q: What are some of the key indicators of weak cipher configurations?
A: Key indicators of weak cipher configurations include:
- Support for outdated or insecure cipher suites: The presence of outdated or known-to-be-vulnerable cipher suites in the supported list.
- Use of weak key exchange algorithms: Employing algorithms such as RSA with weak key lengths or Diffie-Hellman with small group sizes.
- Implementation of weak hashing algorithms: Utilization of outdated or compromised hashing algorithms like MD5 or SHA-1.
- Support for outdated SSL/TLS protocol versions: The service supporting outdated versions like SSLv3 or TLSv1.0, which are known to have significant vulnerabilities.
Q: What steps can I take to remediate weak cipher configurations?
A: Remediation of weak cipher configurations typically involves:
- Updating the server software: Ensure that the server software is updated to the latest version, which often includes security patches and updates to cipher suites.
- Disabling weak ciphers: Configure the server to disable outdated or insecure cipher suites and prioritize the use of strong, modern ciphers.
- Enabling strong key exchange algorithms: Configure the server to utilize strong key exchange algorithms like ECDHE or RSA with sufficient key lengths.
- Using robust hashing algorithms: Implement modern and secure hashing algorithms such as SHA-256 or SHA-3.
- Enabling the latest SSL/TLS protocol versions: Ensure that the server supports the latest SSL/TLS versions, such as TLSv1.2 or TLSv1.3.
Tips for Effective Cipher Detection and Remediation
- Regularly scan your network: Conduct periodic scans using Nmap’s "ssl-enum-ciphers" script to stay abreast of any changes in cipher configurations and identify potential vulnerabilities.
- Prioritize remediation efforts: Focus on remediating the most critical vulnerabilities first, those associated with widely exploited weaknesses or those affecting sensitive services.
- Stay informed about industry best practices: Keep up to date with the latest security recommendations and best practices for secure communication, including cipher suite recommendations and protocol version requirements.
- Implement a comprehensive security strategy: Cipher detection is just one aspect of a comprehensive security strategy. Consider other security measures such as intrusion detection systems, firewalls, and regular security audits.
- Automate security tasks: Leverage automation tools and scripts to streamline the process of cipher detection and remediation, improving efficiency and reducing the risk of human error.
Conclusion: Empowering Security Professionals with Nmap’s Cipher Detection Capabilities
Nmap’s "ssl-enum-ciphers" script stands as a powerful tool in the security professional’s arsenal, enabling the identification and analysis of cryptographic configurations within networked services. By meticulously probing target systems, the script uncovers potential vulnerabilities associated with weak ciphers, outdated protocols, and insecure algorithms.
The insights gained from this analysis empower security professionals to proactively address these vulnerabilities, enhancing the overall security posture of their systems. Regular utilization of this script, coupled with a comprehensive security strategy, plays a pivotal role in safeguarding sensitive data and ensuring the integrity of communication channels in today’s digital landscape.






Closure
Thus, we hope this article has provided valuable insights into Unmasking Vulnerability: A Comprehensive Guide to Nmap’s Cipher Detection Capabilities. We appreciate your attention to our article. See you in our next article!
- 0
- By admin
